

I wanna be able to talk with cats
and (worship) octopuses
Give Children of Time by Adrian Tchaikovsky (and its sequels) a read. Spiders, octopi, and… other.


I wanna be able to talk with cats
and (worship) octopuses
Give Children of Time by Adrian Tchaikovsky (and its sequels) a read. Spiders, octopi, and… other.


Some time back there was an attack on Lemmy where (if I recall correctly) HTML embedded in emoji allowed tokens of users viewing the emoji to get stolen… which included administrators auth tokens. There was much havoc wrecked that evening.
The mitigation for this was “all HTML entities are escaped”. Doesn’t matter where they are - they’re escaped. This sometimes leads to them being doubly escaped when rendering. Less than, ampersand, and greater than all get doubly escaped ( > & < ).
… And that gets interesting as I can’t quite tickle that issue.


If the appearance of some social media is “there is reasonable discussion but as soon as something shows up that’s awful, discussion stops there, but it remains up for all to see” - that’s going to have difficulty brining in new people.
Instance blocking but still giving the appearance of condoning the content is going to lead to what appears to be toxic spaces to everyone who hasn’t taken the time to carefully cultivate their block lists.
Ignoring and personally blocking users and instances means that admins and moderators won’t have as good of a view of the health of the communities when everything ends with a troll comment that no one but new users see.


Jetbrains? Good choice.
They’ve recently released a Rust specific IDE - https://www.jetbrains.com/rust/


You want someone else to pay for the disk space and network availability for your videos?


https://www.stilldrinking.org/programming-sucks
All programming teams are constructed by and of crazy people
Imagine joining an engineering team. You’re excited and full of ideas, probably just out of school and a world of clean, beautiful designs, awe-inspiring in their aesthetic unity of purpose, economy, and strength. You start by meeting Mary, project leader for a bridge in a major metropolitan area. Mary introduces you to Fred, after you get through the fifteen security checks installed by Dave because Dave had his sweater stolen off his desk once and Never Again. Fred only works with wood, so you ask why he’s involved because this bridge is supposed to allow rush-hour traffic full of cars full of mortal humans to cross a 200-foot drop over rapids. Don’t worry, says Mary, Fred’s going to handle the walkways. What walkways? Well Fred made a good case for walkways and they’re going to add to the bridge’s appeal. Of course, they’ll have to be built without railings, because there’s a strict no railings rule enforced by Phil, who’s not an engineer. Nobody’s sure what Phil does, but it’s definitely full of synergy and has to do with upper management, whom none of the engineers want to deal with so they just let Phil do what he wants. Sara, meanwhile, has found several hemorrhaging-edge paving techniques, and worked them all into the bridge design, so you’ll have to build around each one as the bridge progresses, since each one means different underlying support and safety concerns. Tom and Harry have been working together for years, but have an ongoing feud over whether to use metric or imperial measurements, and it’s become a case of “whoever got to that part of the design first.”


APL and J have made there appearance in here with their awkward syntax and have the advantage of being practical languages in actual use.
Esolanguages are often things that are designed to be difficult in some way, shape, or form. Brainfuck is awkward, but it’s the source of some interesting problems that are only practical because it is such a simple language.
The thing is, once you get your head around it, it isn’t too bad of a language.
I was introduced to FRACTRAN (wiki) in Project Euler - https://projecteuler.net/problem=308
That one… still is beautiful and confusing. It’s based on the manipulation of variables through Gödel numbering (wiki). The program: ( 455/33 , 11/13 , 1/11 , 3/7 , 11/2 , 1/3 ) will multiply the exponents of 2a3b leaving the result in 5ab.
The program ( 17/91 , 78/85 , 19/51 , 23/38 , 29/33 , 77/29 95/23 , 77/19 , 1/17 , 11/13 , 13/11 , 15/2 , 1/7 , 55/1 ) will loop forever, however as it runs the state of the program will occasionally be just a power of 2 with all the other powers (variables) being zero. Those values are: 22 , 23 , 25 , 27 , 211 , 213 , … and so on. It computes prime numbers and stores them in the power of 2 before going to compute the next one.
While I understand the idea of Gödel numbering, the manipulation of those numbers through this process still is difficult for me.


https://www.rosettacode.org/wiki/Category:APL and https://www.rosettacode.org/wiki/Category:J for fun links.
ackermann←{
0=1⊃⍵:1+2⊃⍵
0=2⊃⍵:∇(¯1+1⊃⍵)1
∇(¯1+1⊃⍵),∇(1⊃⍵),¯1+2⊃⍵
}
Traditional APL required its own typewriter ball for printing out programs.


He has an iPad 6
I believe you’d be able to load up Swift Playgrounds on that now as a “here’s a place to start” - https://www.apple.com/swift/playgrounds/ - it is a very safe place to start.
In general, I’m gonna ask “why?” for loading up a Linux distribution on a Mac unless there is specific software that you’re after that only runs on Linux. For the most part, launch a terminal and you’re getting 90% of what the Linux experience has to offer (Mac OSX is a unix certified operating system).
I’d look also for games that are programming under the covers or related. Factorio (circuits) and Minecraft (red stone logic) are two that come to mind first.
Shenzen I/O (and the rest of Zachtronics) along with Human Resource Machine and 7 Billion Humans might be a bit more, but also something he could “grow into”.
I would suggest staying as far away from Roblox as possible.


I wrote this a while back… I still think it’s true (though I don’t think its “finished”)
Factorio
So there’s this game I play… just a little bit. Factorio.
In playing this game, I’ve realized that there are several parts of the game play that are directly applicable to software design. The idea of Patterns becomes more clear on how to explain them and how to use them in regular software when one can point to something a bit more concrete (all be it a construct in a virtual world). A visual example of reasonable design and problems of scale are also software design issues that become more apparent with factorio.
Patterns
Patterns are a favorite rant of mine - that developers are asking for a pattern to do something and you take a Something and a SomethingElse and link them together and you’ve got a working application.
Factorio gives me a better way to explain what a Pattern is.
One of the problems that I’ve had in factorio is a pump that flickers on and off rather quickly. This made a mess of the power display (a very high frequency sine wave was evident - determining the actual overall power consumption over time became more challenging) and lights that were hooked up to it to indicate that the pump was on were flickering at a high frequency (a rather annoying strobe).
The cause was that the pump (and light) were connected to a tank containing refined oil. The pump was to pump off excess when it got to 24,000 units. If the tank was at 24,100 units the pump would pump off 200 units putting it at 23,900 and shutting off. One sixtieth of a second later, something would push another 200 units of refined oil into the tank and the pump would trigger on and off for a sixtieth of a second - the flickering and the high frequency showing up in the power.
The solution to this is to use what is known as a Schmitt trigger. This is a circuit that feeds back to itself with a positive feedback loop. When the trigger turns on at a given threshold it will remain on until the value drops below a different threshold. The way that the trigger was set up was so that when the material reached 24,000 units, it would turn the pump on until the level was at 22,000 units.
The way this was implemented was to use a decider combinator which takes a signal as input (the amount of material in the tank) and sends a signal as output (the value 1 in a given channel) based on some logic (the amount of material in the tank is greater than 24,000). Then a second combinator - an arithmetic combinator - would take that signal of 1 and then multiply it by 2,000 and send that result into the input of the decider combinator. The result would be that the signal is now 26,000 and it would run until the material drops to 24,000 in which case the signal from the decider would switch from 1 to 0 and the arithmetic combinator would stop sending the additional 2000 units as a signal… and we would see the real value of the tank at 22,000.
The Schmitt trigger is a Pattern.
It is silly to be suggesting that one would design something based on the answers to “what are useful Patterns when creating an oil processing area?” One doesn’t add something unless its necessary to solve a problem. And one doesn’t go looking for places to use a Schmitt trigger or other Pattern - they are tools for solving specific problems.
Reasonable design
The first base that a person builds is often what is known as a spaghetti base. The layout is ad-hoc. As you need something from somewhere (some iron plates) to get to somewhere else you split off from a convenient, nearby belt with some iron on it and run it over to the place it is needed. It sounds ok at first, but doing this a few dozen times the layout becomes more and more convoluted.
Enter the main bus.
The main bus is a design where there is a large number of belts running down the center of the base and things tap off of it perpendicular for specific factories that build a given item.
The taps off are well researched designs that have a specific fraction of the items shunted off to the factory. Instead of trying to figure out where the iron came from and how to get more iron down to that place maybe a few hundred tiles away, one can look at the main bus and see a dozen tiles and understand what that sub factory is making and how many resources it needs.
The reasonable design allows one to more quickly fix issues of resource starvation and allocation along with refactoring of specific areas of the overall system without worry about impact to things downstream. The base is reasonable.
Problems of scale
After playing a bit and winning the game a time or two, one gets the urge to build BIG. Not these little “launch a rocket every couple of minutes” but rather “launch a rocket every second.”
The design for the one rocket every few minutes is fundamentally different than the design for one rocket every second. The layout of the base for a simple mainline works well - but it doesn’t have the throughput for materials that would enable the launch a rocket every second goal.
For this, one starts building outpost factories that do one thing, and one thing well. This outpost takes iron ore and produces iron plates. That outpost takes iron plates and copper plates and produces green circuits. So on and so forth.
This is a very different design - switching from a main bus to train logistics (trains become the way to move massive amounts of material). The very structure of the base for a megabase vs a regular base shows differences at every level.
Many times one reads about developers having difficulties with microservices and trying to build something to scale to 1000 users per second. And then comes the moment when they are asked how many users per second they’re currently getting and the answer is something along the lines of “Um, we’re getting maybe 5 a second on a good day… but we’re getting ready for being Amazon or Twitter scale.”
Design for what works. It is often easier to redesign a working system up than it is to try to start out with the megabase or amazon scale system and fight all those little problems of outpost base train networks and microservices that you haven’t encountered before in a working system.
It took them years ago. From 2015 : An NPR Reporter Raced A Machine To Write A News Story. Who Won?
And its only gotten better: Can ChatGPT write a podcast episode? Can AI take our jobs?


IRC is fine for almost synchronous communication - but dealing with things that work on the timescale of days or weeks, IRC becomes difficult to maintain a discussion about a fix or feature over that timeframe that includes all the interested participants.
Mailing lists often come with an archive and a sufficiently large project will have multiple lists for different aspects of the project. Consider gcc ( https://gcc.gnu.org/lists.html )and you’ll see that bugs and patches are their own lists. Going into there you can also see the archives for the project… and if the mailing list software has support for it, viable by thread https://gcc.gnu.org/pipermail/gcc-bugs/
https://lkml.org/lkml/2013/11/25/519 is another fun read (that entire thread).
git has support for (and was originally used via) email. git send-email (docs) and git am (docs) are part of its original functionality and that workflow can make use if it.
I’m personally most comfortable with GitHub or GitLab, followed by email. An IRC or discord project lacks the ability to properly research the “why was this done that way back in 2016”… unless the project doesn’t aspire to be a long lived open source project.
Managing email is something that should be considered as part of this. Setting up a separate email address for that project, or using the + addressing as part of the email to make it so that your email filters can operate on them better (Exchange, gmail). This may require deeper familiarity with email clients than is common today - smart mailboxes in Mac Mail, client side rules in Exchange, or old school procmail with a shell account.
Are you sure about chat mode working (correctly) that way? This one is at the top…
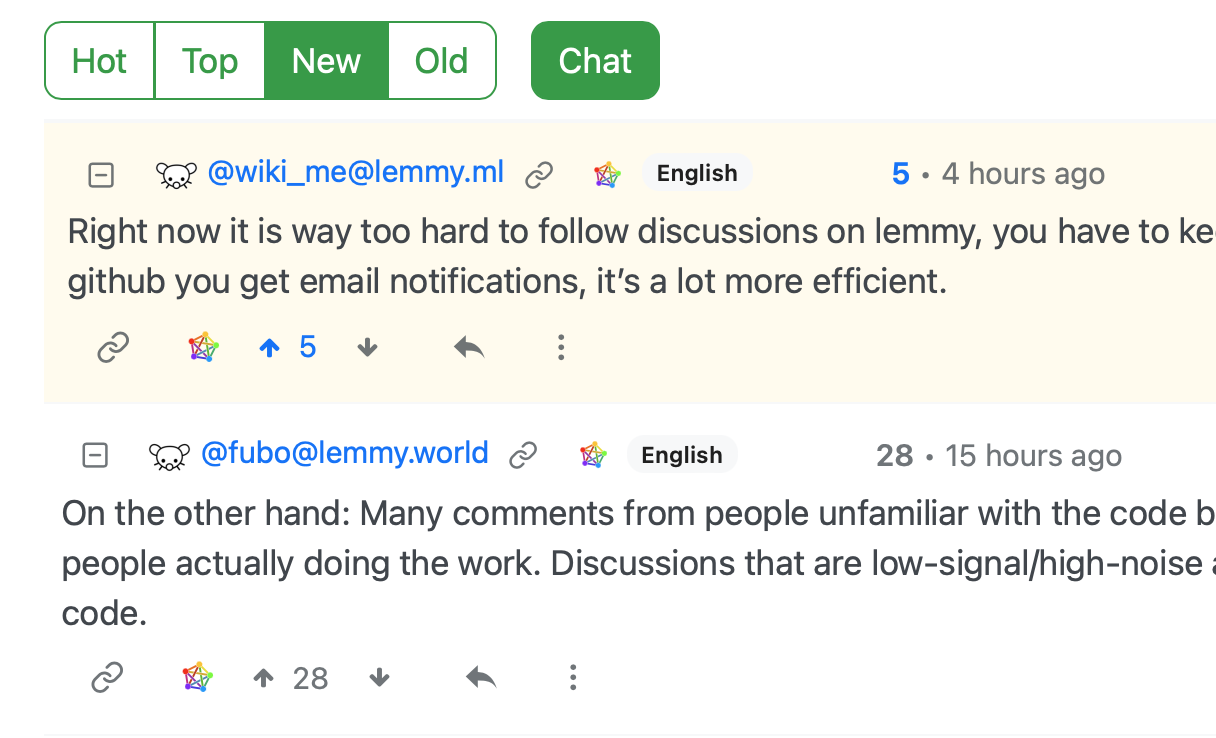
But at the bottom of the screen is:
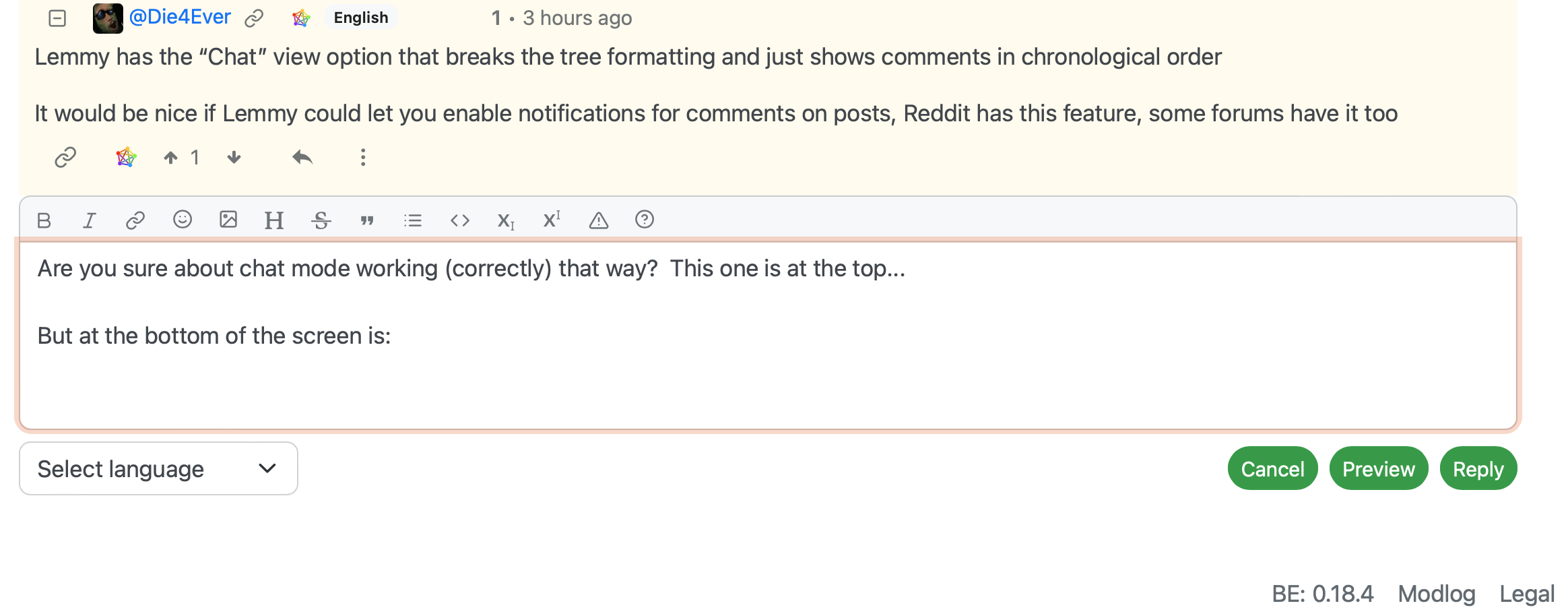
This doesn’t appear to be in chronological order.


Unless you specifically pay for the rights transfer (and it’s not cheap), the photographer owns the copyright.
Under federal law, if there is no agreement to the contrary, your wedding photographer, or any photographer for that matter, owns the pictures that they take. This means that they have the sole right to copy and distribute the photos, including potentially the right to sell the photos, to publish the photos in any form, and to reproduce the photos either electronically or in a printed hardcopy version. And even more importantly, copyrighted material cannot be reproduced or copied without permission from the photographer.
…
Generally, photographers do not like to offer their services to clients through a Work for Hire Agreement. This may be partly related to their desire to require clients to purchase prints and books directly from them. Many photographers, however, do not want to completely relinquish their rights because they may be trying to build or protect their reputation.
Granted, this a US take and may vary by country…
If you are a couple getting married in Australia, the copyright law automatically assigns copyright to you and not the photographer. However, most professional photographers will have their clients sign a contract that reassigns the copyright to the photographer. Now let’s be very clear, this is not the photographer being shady or deceptive in anyway. It’s simply to protect their work, the photographs in this case, that they created.


2- positive supply-chain validation. Not important for the majority of people, but for those who require a little more security, they can be a little more sure that their device isn’t compromised from illegitimate parts. I imagine this to be a fringe benefit for executives and the like
Anecdotally, many years ago I had a Mac laptop that was fairly new but I ran it as what amounted to a portable desktop. It was plugged in 99% of the time. A few months after I got it I had an issue with one of the fans. Instead of taking it to the Apple Store that was 90 miles away (I was living and working in a small town then), I took it to the local computer repair… and they fixed it it.
Afterwards, while I didn’t use batteries much, it seemed off.
Another two years and I had moved to a larger city and took my laptop into the local Apple Store for them to replace a fan that was not operating strongly enough. The repair tech commented that I had a sub par third party and while it should be replaced as its battery health was very low, it wouldn’t be covered under warranty because it clearly wasn’t an OEM Apple part.
I strongly suspect that the repair shop had swapped my new battery out for an old one and hoped I wouldn’t notice because I didn’t use it in that capacity. I can’t prove anything and the shop had gone out of business.
This is anecdotal and batteries for laptops don’t get pairing the same way phones do… but this sort of thing happens.
No.
The nature of the checksums and perceptual hashing is kept in confidence between the National Center for Missing and Exploited Children (NCMEC) and the provider. If the “is this classified as CSAM?” service was available as an open source project those attempting to circumvent the tool would be able to test it until the modifications were sufficient to get a false negative.
There are attempts to do “scan and delete” but this may add legal jeopardy to server admins even more than not scanning as server admins are required by law to report and preserve the images and log files associated with CSAM.
I’d strongly suggest anyone hosting a Lemmy instance to read https://www.eff.org/deeplinks/2022/12/user-generated-content-and-fediverse-legal-primer
The requirements for hosting providers are https://www.law.cornell.edu/uscode/text/18/2258A
(a) Duty To Report.—
(1) In general.—
(A) Duty.—In order to reduce the proliferation of online child sexual exploitation and to prevent the online sexual exploitation of children, a provider—
(i) shall, as soon as reasonably possible after obtaining actual knowledge of any facts or circumstances described in paragraph (2)(A), take the actions described in subparagraph (B); and
(ii) may, after obtaining actual knowledge of any facts or circumstances described in paragraph (2)(B), take the actions described in subparagraph (B).
(B) Actions described.—The actions described in this subparagraph are—
(i) providing to the CyberTipline of NCMEC, or any successor to the CyberTipline operated by NCMEC, the mailing address, telephone number, facsimile number, electronic mailing address of, and individual point of contact for, such provider; and
(ii) making a report of such facts or circumstances to the CyberTipline, or any successor to the CyberTipline operated by NCMEC.
…
(e) Failure To Report.—A provider that knowingly and willfully fails to make a report required under subsection (a)(1) shall be fined—
(1) in the case of an initial knowing and willful failure to make a report, not more than $150,000; and
(2) in the case of any second or subsequent knowing and willful failure to make a report, not more than $300,000.
Child Sexual Abuse Material.
Here’s a safe for work blog post by Cloudflare for how to set up a scanner: https://developers.cloudflare.com/cache/reference/csam-scanning/ and a similar tool from Google https://protectingchildren.google
Reddit uses a CSAM scanning tool to identify and block the content before it hits the site.
https://protectingchildren.google/#introduction is the one Reddit uses.
https://blog.cloudflare.com/the-csam-scanning-tool/ is another such tool.


I looked at it when it came out. The problem is that taking classes back in the early 90s with computer programming - the CS department was an offshoot of the Math and Statistics departments rather than engineering (the engineering department was hardware focused - designing chips and circuit boards)… and so I don’t have the deep physics background that the FE exam expects you to have prior to taking the PE exam.
If I had taken electrical and computer engineering… well, assuming that I got through the math (had to take the CS numerical methods class three times)… maybe. But if people want to complain about the irrelevance of reversing a list or describing two different approaches to balanced trees… they’d probably complain more about being tested on generators and RC frequency response in low pass filters even if you only have to take it once.
Copyright DMCA filings never went to the mods. Those are legal requests and not handling properly can be a nightmare complete with lawyers.
Those requests went via https://support.reddithelp.com/hc/en-us/requests/new - no volunteer mods or API requests involved.